GILES RAFFERTY, Corporate Communication and Media Advisor
Cybersecurity is back at the top of the news agenda. The Albanese Government is seeking to tackle ‘Doxing’, which is publicly revealing identifying material about someone without their consent; the AFP has helped to smash global ransomware gang Lockbit and the hacker claimed to behind the massive Medibank data breach in October 2022 has been detained in Russia. Likely of more interest to listed companies is the release of the ‘Notifiable Data Breaches Report: July to December 2023’ by Office of the Australian Information Commissioner (OAIC).
The Federal Government’s Notifiable Data Breach (NDB) scheme is 5 years old, and the expectation is the companies that sit under the scheme will fully understand their obligations. Every private or public company with annual turnover of $3 million or more must report cyber breaches that are likely to result in harm to individuals whose personal data is compromised to the OAIC as soon as they become aware of a breach. Companies covered by the NDB must also notify the individuals affected by a breach and offer recommendations to them about how best to protect themselves.
More than 5000 Data Breach Notifications
While Optus and MediBank have the unenviable position of being the Australian poster children for data breaches, the information stolen from them in 2022 covered nearly half the population of Australia, the OAIC has received over 5000 data breach notifications in the 5 years since the NDB was launched.
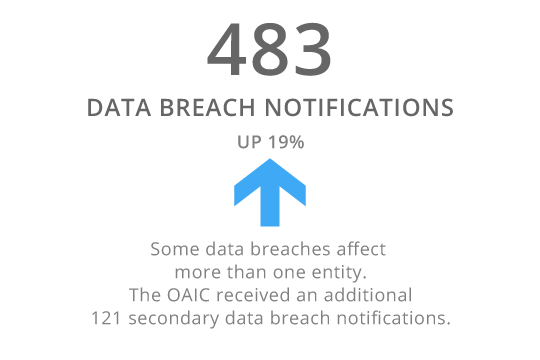
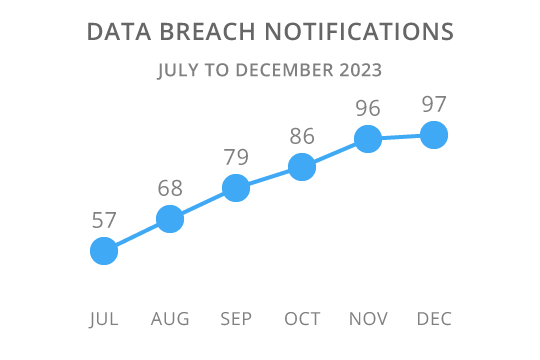
The trend in the most recent NDB report for the July to December 2023 period was for a 19% increase in the number of notifications to 483, (see figure 1), which follows a decline of 16% in notifications to 407 in the January to June 2023 period. This pattern of a greater number of breaches being reported in the second half of the calendar year has persisted since the inception of the NDB in 2018.
Figure 1
Interestingly, despite the strong upward trend in monthly reporting over the final 6 months of 2023, the total number of data breaches reported under the NDA for the year was unchanged from the 890 reported in 2022 and the 900 notifications in 2021 but was belowthe 1,051 notifications in 2020, the largest number of notifications in a 12 month period since the NDB was launched.
Multi-Party Breaches Highlight Supply Chain Risk
The risk from outsourcing personal information handling to third parties was brought into focus in the second half of 2023 when the OAIC received 121 secondary data breach notifications compared to 29 in the first half. A secondary notification is when the OAIC receives a report from additional entities affected by a breach that has already been reported. The sharp increase in secondary notifications may be linked to an increase in the level of multi-party breaches, most of which result from a breach of a cloud or software provider.
The OAIC Commissioner has identified multi-party breaches as a key contributor to the increase in complexity, scale and impact of data breaches and stated the OAIC will look to escalate regulatory actions, including the option of initiating Federal Court proceedings.
“Organisations need to proactively address privacy risks in contractual agreements with third-party service providers.
“This includes having clear processes and policies in place for handling personal information and a data breach response plan that assigns roles and responsibilities for managing an incident and meeting regulatory reporting obligations.”
Australian Information Commissioner, Angelene Falk
Civil Penalty Proceedings
Companies may face legal action if they fail to have processes in place to ensure they have a considered and up‑to‑date data breach response plan, as was the case with Australian Clinical Labs Limited (ACL).
On 3 November 2023, the Commissioner announced the commencement of civil penalty proceedings in the Federal Court against ACL following a February 2022 data breach that resulted in sensitive information being published on the dark web.
Commissioner alleges that ACL:
-
- failed to conduct a reasonable and expeditious assessment,
- failed to notify the Commissioner as soon as practicable.
The Federal Court can impose a civil penalty of up to $2,220,000 for each contravention.
Healthcare Services top the table for breaches
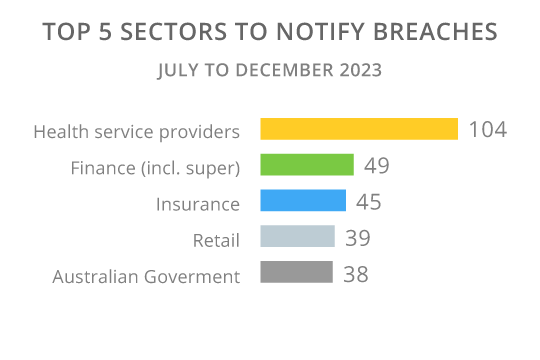
In the 5 years that reporting data breaches has been mandatory Healthcare Services have consistently accounted for the greatest number of reports. In the July to December 2023 period Healthcare Service providers reported 104, (see figure 2), up from 63 in the first half of CY 2023. The Financial Services sector, including superannuation, has consistently reported the second most breaches, 49 in the second half of CY2023, although this was down from 54 in the first half.
Aside from Healthcare and Finance, other industries have made periodic appearances in the top 5 sectors include the Insurance sector in 2023, 2022 and 2020, Education between 2018 and 2021; the Australian Government in 2023 and 2021; retail in 2023; Recruitment in 2022; Personal Services in 2019 and Business and Professional Services in 2018.
Figure 2
Sources of Data Breaches
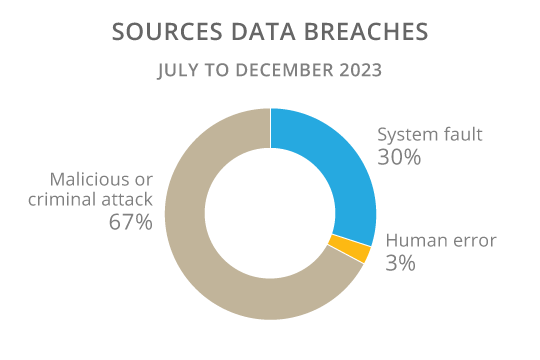
Malicious or criminal attacks remain the leading cause of data breaches (see figure 3). Between July and December 2023 there were 322 malicious or criminal attacks reported, (310 in1H23). The increase in breaches relating to human error (+36%) and system fault (+21%) were both material.
Figure 3
Of the 144 human error incidents reported, 46% related to personal information being sent to the wrong e-mail recipient, 20% to the unintended release or publication of data and 10% to personal information being sent to the wrong recipient via traditional mail.
65% of breaches in the second half of CY 2023 affected 100 people or less (63% in 1H23).
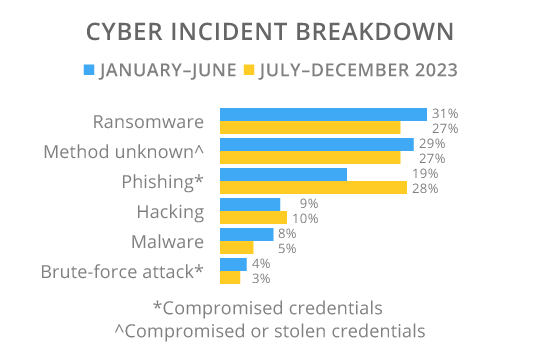
Cyber security incidents accounted for 44% of data breach notifications (211) between July and December 2023 (see figure 4). This is consistent with the first half of 2023 (42%) and 2022 (43% of notifications).
The following chart highlights the most common types of cyber incident over the past year. Phishing attacks were the most common reported incidents in 2H23 taking over from Ransomware attacks, which dominated in the first half of 2023.
Figure 4
Strengthening enforcement
Following the publication of the Attorney-General’s Privacy Act Review in February 2023 the Australian Government committed to progressing work on privacy protections for individuals and ensure Australian businesses have clarity about how to best protect this information. In September 2023, the government agreed in principle to proposals to strengthen the NDB and is currently conducting targeted consultations to support the development of reforms.
The government is looking to sharpen the OAIC’s teeth and after 5 years of the NDB scheme there is an expectation that organisations will understand and comply with their obligations or potentially face legal action.
For listed companies this makes it more important than ever that a cyber-incident response plan is put in place and regularly tested, built on the advice of external advisers and incorporating a well thought out communication strategy. Bringing in advisers with experience in crisis communication to support the internal team is strongly recommended. There is only one opportunity to get the response right so using it as an exercise to test whether or not the team can cope almost guarantees a disappointing outcome.