VICTORIA GEDDES, Executive Director
It’s exactly two years now since the Federal Government introduced its Notifiable Data Breach (NDB) scheme. It requires every private and public company with annual turnover of $3 million or more, listed or not, to report cyber breaches that are likely to result in serious harm to individuals whose personal information is involved in the breach. A company must notify the Office of the Australian Information Commissioner (OAIC) and the affected individuals as soon as they become aware of a breach. The notification must include recommendations about the steps individuals should take to protect themselves.
Data Breaches That we Know About
In the first two months of 2020 there have already been a number of high profile cybersecurity attacks, the most notable being the ransomware attack on Toll Holdings which forced it to take down many of its delivery and tracking systems, leaving it unable to tell customers where their parcels were. In December last year Monash IVF, one of Australia’s largest IVF providers, warned patients that it could not rule out the possibility their personal information may have been breached following a widespread cyberattack on staff emails the previous month. In June last year Australian National University (ANU) had 19 years of data relating to around 200,000 current and former students and staff accessed. The data breach included personal details, contact information, tax file numbers, bank account numbers, passport details and academic records with China regarded as the key suspect. The previous month Aussie success story, Canva, with 139 million users had hundreds of thousands of users’ usernames, e-mail addresses, passwords and, in some cases, users’ artwork stolen. These are however only a few of the nearly 1000 breach incidents reported last year.
The Stats So Far
The Office of the Australian Information Commissioner (OAIC) provided an update last week on the number of reported data breaches reported under the mandatory scheme since it began in February 2018.
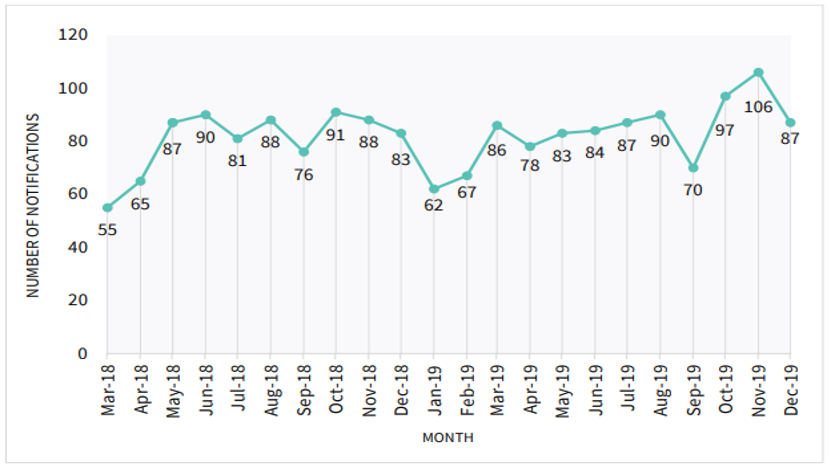
In 2019 there were 997 breaches reported, an increase of 23% on the 10 months of data the previous year (812 breaches). This compares with 114 reported in 2017 under the previously voluntary reporting scheme.
The trend is increasing with the highest number of reported data breaches (106 notifications) occurring in November 2019 ― the most reported in any calendar month since the scheme began.
Majority of breaches (62%) affect less than 100 people
The scale of people affected by an individual breach tends to be concentrated in small clusters. A quarter of all breaches involved the release of information on only one person with another 36% affecting 2 to 100 people. This data is consistent with the previous year including that large scale breaches (those involving information relating to groups of people greater than 100,000), comprise just 1% of all notifications.
Most common data breached is Personal Contact Information (40%)
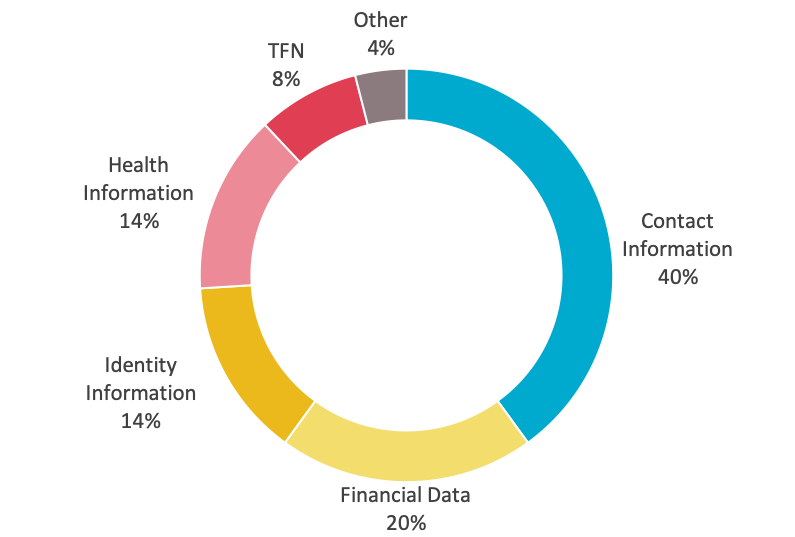 The majority of data breaches in 2019 involved contact information (40%) or an individual’s name, email address, home address or phone number. This is distinct from ‘identity’ information (14%) which refers to such things as driver’s licence numbers and passport numbers. One in five reported breaches involved financial details such as bank account or credit card numbers and 14% involved health Information. This data is similar to 2018 except for an encouraging drop in identity information breaches from 16% to 14%. By contrast breaches of health information rose from 12% to 14%.
The majority of data breaches in 2019 involved contact information (40%) or an individual’s name, email address, home address or phone number. This is distinct from ‘identity’ information (14%) which refers to such things as driver’s licence numbers and passport numbers. One in five reported breaches involved financial details such as bank account or credit card numbers and 14% involved health Information. This data is similar to 2018 except for an encouraging drop in identity information breaches from 16% to 14%. By contrast breaches of health information rose from 12% to 14%.
Healthcare (37%) continues to lead the Number of Breach Incidents by Industry
Since mandatory reporting was introduced the private health sector has consistently accounted for the greatest number of reported breaches. In 2019 they accounted for 37%, followed by the Finance sector (including superannuation) with 25%. Professional services firms in the legal, accounting and management services sector and the private education sector each accounted for 15% of all incidents.
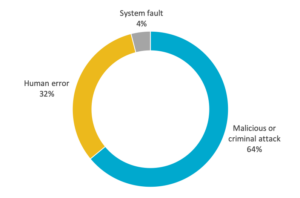
Majority of breaches (63%) are the result of criminal or malicious intent
Data released for 2019 shows an increase in the number of breaches due to malicious or criminal attacks from 59% in 2018 to 63%. Breaches due to human error fell from 36% to 33%.
Phishing remains the weak link in Cybersecurity
The OIAC has provided increased visibility on exactly how the various data breaches occur in their latest report.
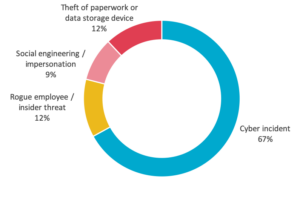
Cyber incidents (67%) were the largest source of malicious and criminal attacks from July to December 2019, with phishing, malware, ransomware, brute-force attack and compromised or stolen credentials the main source of the data breaches.
Rogue employees or theft of paperwork or data storage devices were also significant sources (24%) of malicious or criminal attacks.
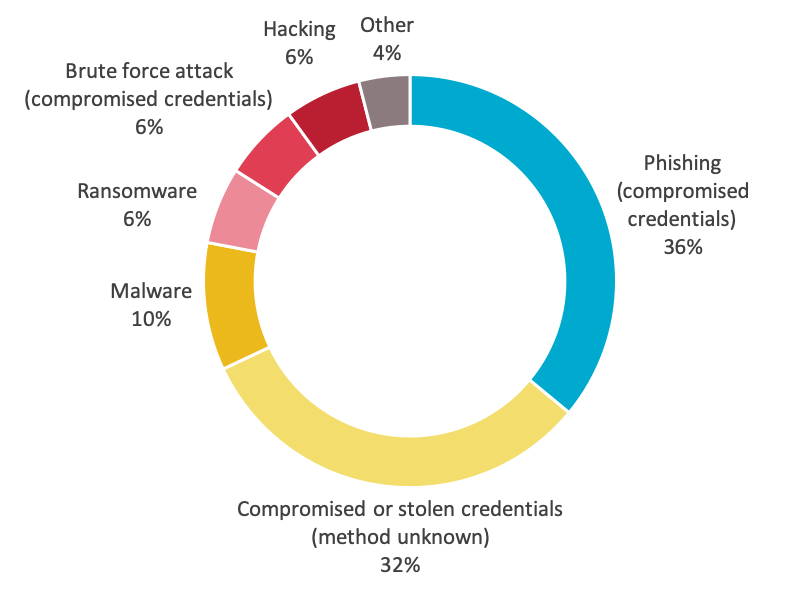
The majority of cyber incidents were linked to the compromise of credentials through phishing (36%) which is the attempt to get usernames, passwords or credit card details by sending a request for information that looks like it comes from a trustworthy source, as well as through malware (10%) and brute-force attack (6%).
In many of these incidents access was gained to personal information stored in email accounts. This can include financial information, tax file numbers, identity documents and health information, which can be exploited by malicious actors who gain access to inboxes. Ideally such information should be stored in a secure document management system and the emails deleted from both the inbox and sent box.
Of particular concern however is that, in a third of all cyber attacks, the entity experiencing the breach was unable to identify how the malicious actor obtained the compromised credentials.
Awareness is the first level of defence
The (NDB) scheme and the data it collects provides us with an increased level of awareness about the problem that we didn’t have 2 years ago. It has done this by setting the threshold for reporting a cybersecurity breach higher than anywhere else in the world. This is the likelihood of a breach causing harm which includes when a device containing customers’ personal information is lost or stolen; a database containing personal information is hacked or when personal information is mistakenly provided to the wrong person through human error.
What we now know without a shadow of a doubt is that cyber attacks are a real risk to every company’s operations and reputation. Putting in place and testing a cyber incident response plan, built on the advice of external advisers and incorporating a well thought out communication strategy has never been more important.