As we mark the one-year anniversary of the introduction of the Federal Government’s Notifiable Data Breach (NDB) scheme, the headlines focused on cybersecurity breaches seem to be coming thick and fast. The attack in early February 2019 on the Australian Federal Parliament’s computer network, has been identified by Prime Minister Scott Morrison as the work of a “sophisticated state actor”. It is believed a more recent attempt to hack Toyota Australia, discovered on 19 February, failed to access any sensitive information but some of the car maker’s internal systems were still down as the month drew to a close. The hackers that paralysed the Melbourne Catholic Archdiocese’s internal IT systems late last year seem to be common or garden criminals looking to extort a ransom.
The introduction of the NDB scheme is a Cybersecurity development we, at FIRST Advisers have been monitoring closely. We have presented on the subject at AIRA; contributed to ASX panel discussions; written articles for the Listed@ASX magazine and surveyed ASX 300 companies to assess their readiness for mandatory data breach reporting.
The NDB scheme requires every private and public company with annual turnover of $3 million or more, listed or not, to report cyber breaches that are likely to result in serious harm to individuals whose personal information is involved in the breach. A company must notify the Office of the Australian Information Commissioner (OAIC) and the affected individuals as soon as they become aware of a breach. The notification must include recommendations about the steps individuals should take to protect themselves.
One year on, the threat of cyber-attacks is far greater than expected
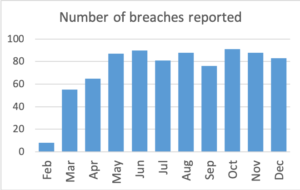
The OAIC predicted that the number of reported breaches under the mandatory scheme in 2018, would be double the 114 reported in 2017 under the previously voluntary reporting scheme. The data for 2018 shows there were a total of 812 breaches reported, up to December 31st2018, an increase of close to 700%!! And that was for less than a full 12-month period, as mandatory reporting only commenced on 22 February 2018.
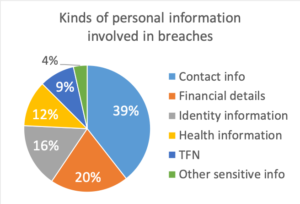
The majority of data breaches to date have involved contact information (39%) or an individual’s name, email address, home address or phone number. This is distinct from ‘identity’ information (16%) which refers to such things as driver’s licence numbers and passport numbers. One in five reported breaches involved financial details such as bank account or credit card numbers and a little over one in 10 involved health information.
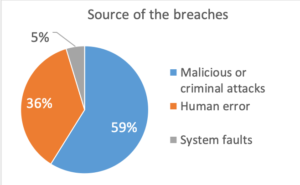
The majority of breaches are the result of criminal or malicious intent
In 2018, malicious or criminal attacks accounted for a significant majority of all breaches (59%) with human error a distant second (36%). Almost a quarter of all breaches involved the release of information on between 100 and 1000 people. This was closely followed by notifications relating to a single individual (23% of reported breaches) while large scale breaches (those involving information relating to groups of people greater than 100,000), were just 1% of all notifications.
Healthcare leads the Number of Breach Incidents by Industry
Since mandatory reporting was introduced on 22 February, three sectors have accounted for almost half (46%) of all breaches. Health Service providers have consistently led the pack representing 1 in 5 notifications, followed by the Finance sector on 15%. Professional services firms in the legal, accounting and management services sector, accounted for a little over 1 in 10 of all incidents.
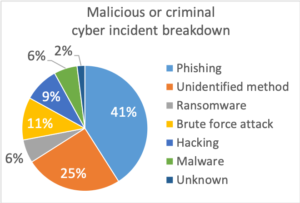
Phishing rules in Cyberland
Within the cyber incidents reported as a malicious or criminal attack between Q2 and Q4 of 2018, the quarters for which there is complete data, phishing was the most common form of attack (41%). Phishing is the attempt to get usernames, passwords or credit card details by sending a request for information that looks like it comes from a trustworthy source.
In a quarter of criminal or malicious cyber-attacks the method used to compromise or steal credentials had not been identified while only 11% of incidents were Brute Force Attacks, where an attacker repeatedly tries various different usernames and passwords to gain unauthorised access to sensitive information.
So are there more attacks or more awareness
The (NDB) scheme sets the threshold for reporting a cybersecurity breach as the likelihood of a breach causing harm. This threshold places Australia ahead of most other countries in terms of recording cyber-attacks and by making reporting mandatory within a 72-hour window of a company becoming aware of an attack. As a result the NDA scheme removes the need for a company to make a judgement about how material a breach is.
Any data breach that ‘is likely to result in serious harm’ must be reported and this includes when a device containing customers’ personal information is lost or stolen; a database containing personal information is hacked or when personal information is mistakenly provided to the wrong person through human error.
While the statistics from 2018 undoubtedly show a startling increase in reporting of data breaches, it is not clear if this is the result of the NDA scheme shining a brighter light on an existing problem or that there has been an actual step change in the number of cyber-attacks. It is likely to be blend of both.
What is clear is cyber-attacks are a real risk to every company’s operations and reputation. Putting in place and testing a cyber-incident response plan, built on the advice of consultants, such as FIRST Advisers, who have developed a deep understanding of the issues, and incorporating a well thought out communication strategy has never been more important.