Victoria Geddes, Executive Director, Writing for the Autumn 2018 Issue of Listed@ASX
On February 22, 2018 the Federal Government’s new Scheme for the mandatory reporting of cybersecurity breaches that result in the loss of personal data came into effect. Every private and public company with annual turnover of $3 million or more, listed or not, is now required to report a cyber breach to the Office of the Australian Information Commissioner (OAIC) and notify affected customers as soon as they become aware of a breach.
The threshold for notification under the new Act is more onerous than most other global jurisdictions, with the test based on whether the breach “is likely to result” in serious harm to an affected individual. Mandatory reporting relieves companies from having to make judgement calls about materiality – ANY breach that ‘is likely to result in serious harm’ to an individual will be reportable. This could occur when there is unauthorised access to, disclosure or loss of customer information held by an entity. Such information includes personal details, credit reporting information, credit eligibility information, and tax file number information. Companies must report the breach within 72 hours.
The Score Card One Month In
Based on experiences overseas the OAIC optimistically predicted last year that the new mandatory requirements for notification would double the number of reported incidents each year. On 11 April the OAIC released data for breach notifications for the first 5 weeks of operation – 63 notifications compared to 114 for the whole of the 2017 financial year under the previously voluntary scheme!
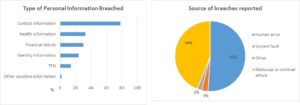
The majority of data breaches to date have involved contact information (78%) or an individual’s name, email address, home address or phone number. This is distinct from ‘identity’ information (24%) which refers to such things as drivers licence numbers and passport numbers. Health information and financial details such as bank account or credit card numbers were each represented in around a third of reported breaches.
Human error (51%) and malicious or criminal attacks (44%) accounted for almost all of the breaches. Just over half of the notifications involved the release of personal information of between 1 and 9 individuals with 27% of notifications involving more than 100 individuals. The scheme has yet to deal with a large scale breach involving more than 100,000 people and that will be when the communications component of an organisation’s cyber incident response plan (assuming they have one) is really put to the test.
Healthcare leads the Number of Breach Incidents by Industry
Australia’s mandatory reporting data highlighted that 5 sectors accounted for 66% of all breaches with Health Service providers leading the pack (23%). This is not dissimilar to the experience reported globally for 2017 where the top 5 industry sectors accounted for 72% of all breach incidents with Healthcare (26%) also topping the list by some margin.
Where Australia’s stats differ markedly from the global experience is the level of data breaches coming from professional services firms in the legal, accounting and management services sector which comprised 16% of all incidents compared with only 5% globally. It has to be acknowledged however that this is a small sample and it would be unwise to be too definitive about drawing conclusions so early in the scheme’s implementation.
How prepared are Australian listed companies for mandatory reporting?
FIRST Advisers surveyed the ASX300 companies during September and October 2017, seeking feedback on their readiness for Mandatory Reporting of Cybersecurity breaches in 2018. Perhaps not unsurprisingly, the responses were sharply divided according company size and sector.
Small cap companies and those in the metals and mining sector had yet to establish frameworks for reporting on or addressing this risk. Large cap companies, particularly those in the Financials and AREIT sectors, were however much more confident that they were properly prepared for a cyber incident. They were generally well organised (83%), with comprehensive response plans in place that covered all key stakeholders. The less well-resourced small cap companies were struggling to meet this standard (23%).
The survey gathered feedback on a range of issues including management awareness of and preparedness for the change in reporting protocols, how they communicated their risk profile to the investment community and whether they had a cyber incident response plan and crisis management plan in place which was periodically updated and tested. The results were summarised in the report “Listed Company Readiness for Mandatory Reporting” which is freely available here: Cyber Security Survey.